A common requirement with Site-to-Site tunnels is access-control through the tunnel. One strategy to accomplish this might be to have a rather complex crypto ACL. But this leads to additional administration overhead as there is actually a pair of IPsec SAs for each active
entry in the crypto ACL. The proper way to limit traffic through a Site-to-Site tunnel with the ASA is to apply a filter via group policy. In this section of the lab, you will prevent Site1 systems from reaching the management subnet.

- 8.4.1.3 Lab -Configure Site-To-Site VPN Using CLI instructor version - Free download as Word Doc (.doc /.docx), PDF File (.pdf), Text File (.txt) or read online for free. 8.4.1.3 Lab -Configure Site-To-Site VPN Using CLI instructor version.
- This is an OpenVPN client docker container. It makes routing containers' traffic through OpenVPN easy. What is OpenVPN? OpenVPN is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities.
8.4 1.3 Lab Site To Site Vpn Using Cli Commands
1. Create an ACL which denies access to 10.10.2.0/24 for use as a filter for the Site1 VPN
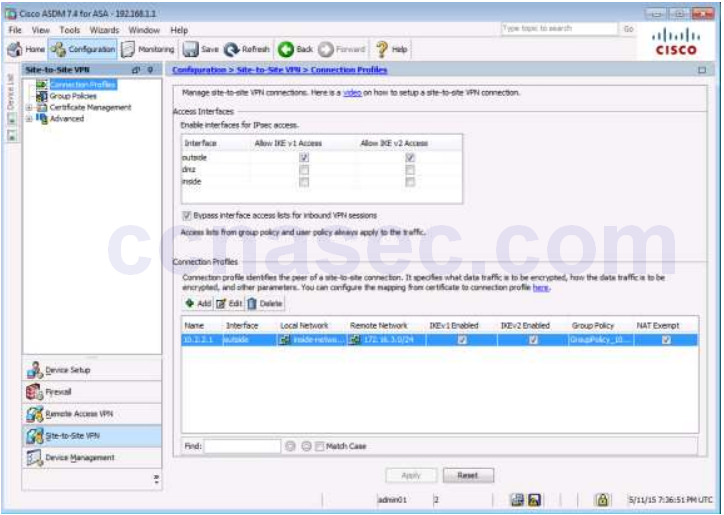
Navigate to Configuration > Site-to-Site VPN > Advanced > ACL Manager
The table of ACLs defined on the ASA appears.
Click Add > Add ACL.
Enter the name Site1-VPN-Filter and click OK.
View 8.4.1.3LabSTU.pdf from SEC 150 at Pitt Community College. CCNA Security Chapter 8 Lab – Configuring a Site-to-Site VPN Using Cisco IOS This lab has been updated for use on.
With Site1-VPN-Filter highlighted in the table, click Add > Add ACE.
Define the first Access Control Entry as follows:
• Action: Deny
• Source: Any
• Destination: 10.10.2.0/24
• Service: ip
Leave other options at their default values and click OK.
Lab 8.4.1.3 Configure Site To Site Vpn Using Cli
Select the first line in the Site1-VPN-Filter and select Add > Add ACE.
Define the first Access Control Entry as follows:
• Action: Permit
• Source: Any
• Destination: Any
• Service: ip
Leave other options at their default values and click OK.
Click Apply.
2. Modify the group policy for Site1-VPN, and select the new ACL as the filter:
Navigate to Configuration > Site-to-Site VPN > Group Policies
Select the Site1-Policy and click Edit.
Modify the group policy as follows:
• IPv4 Filter: Uncheck Inherit and select Site1-VPN-Filter
Leave the other values at their defaults and click OK.
Click Apply.
The policy is defined, but it won’t take effect until the next time the Site1 VPN tunnel is negotiated.
3. “Bounce” the Site1 tunnel:
Navigate to Monitoring > VPN > VPN Statistics > Sessions
Set the filter to IPsec Site-to-Site.
If the tunnel to 200.200.20.2 is still active, click Logout.
Posted in ASA Site-to-Site VPN, Network Security